An Unpatched System is the Increasing Source of Defacement
The following image contains the comparison of the number of defacements grouped by the attack method in 2010 and 2020.
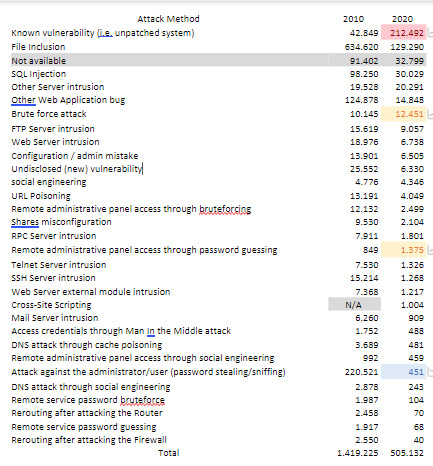
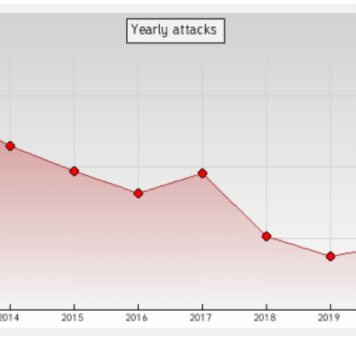
It’s clear that the number of defacement notifications in zone-h.org is significantly decreased 3 times in 10 years apart. Most of the attack methods are relatively decreased, except the unpatched system is significantly increased. It represents exploitation on an out-of-date local kernel.
The hacks are not only happened to an open-source operating system (i.e. Linux) but to another OS (e.g. Windows), as well. Updating the system periodically by Administrators is not enough most of the time. Defacers still have many ways to attack.
These attacking to servers methods inclusive of file inclusion, SQL injection, and application bug are still at the top ranks of the attack methods used by defacers (as shown by the above image) to gain first access into the server.
We all know that the very first hole to gain access to the server lies in the website code. For example, due to a remote upload flaw, it allows the defacers to upload anything to the CMS folder without proper credential check.
From our development side, we still keep risky behavior. All this time, some developers are still coding unsafely, keeping tons of the remote and local file inclusion and SQL injection, so the attackers use it as the first step to gain access into the server OS.
Even though application and infrastructure nowadays are more advanced compared to ten years ago, fighting defacement is a never-ending activity. While fixing all the abovementioned old bugs, more new bugs still possible to appear, and it might open new ways for hackers, and the defacement will keep appearing.
Therefore, we suggest you use SentryPage, a relevant monitoring tool for your website. It will check periodically your page and send alerts in no time whenever your pages are defaced. The faster you aware, the more time you can have to handle the defacement.
